Computer System Validation: A Comprehensive Training Framework
Computer System Validation (CSV) is the cornerstone of regulatory compliance in pharmaceutical, medical device, and biotech industries. This comprehensive training program equips quality assurance and compliance professionals with the critical knowledge and practical skills needed to validate and maintain computerized systems throughout their lifecycle. Built on the System Development Life Cycle (SDLC) framework and aligned with GxP regulatory requirements, this curriculum ensures a thorough, risk-based approach to system validation that protects product quality, data integrity, and patient safety
Course Overview: Building Validation Excellence
Structured Learning Approach
The curriculum is meticulously designed around industrystandard frameworks and regulatory expectations. Each module
builds progressively on foundational concepts, ensuring
participants develop both theoretical understanding and
practical implementation skills.
From regulatory foundations through operational maintenance,
the course follows the natural progression of a validation project,
mirroring real-world implementation scenarios that professionals
encounter in GxP environments.
Risk-Based Methodology
Central to modern CSV practice is the risk-based approach
emphasized throughout the training. Participants learn to focus
validation efforts where they matter most4on critical system
functions that directly impact product quality, data integrity, and
patient safety.
This pragmatic approach, endorsed by regulatory authorities
worldwide, optimizes resource allocation while maintaining
robust compliance standards and enhancing overall system
assurance.
Module 1: Regulatory Foundation & Standards
Understanding the regulatory landscape is essential for effective computer system validation. This foundational module establishes the
legal and industry expectations that drive all validation activities in GxP environments.
GxP Principles
Comprehensive coverage of Good Practices4GMP, GLP, and
GCP4and their application to computerized system design,
implementation, use, and maintenance throughout the entire
system lifecycle.
FDA 21 CFR Part 11
In-depth exploration of US regulations governing Electronic
Records and Electronic Signatures, including audit trail
requirements, security controls, and data integrity safeguards.
EU Annex 11
Detailed review of European Union guidelines on
computerized systems, with comparative analysis against FDA
requirements to support global compliance strategies.
GAMP 5 Framework
Mastery of the industry-standard risk-based approach for
achieving compliant GxP computerized systems, including
software categorization and validation effort determination.
GAMP 5: The Industry Gold Standard
Risk-Based Validation Approach
GAMP 5 (Good Automated Manufacturing Practice) represents the
pharmaceutical industry’s consensus on how to achieve compliant
computerized systems efficiently. This framework introduces a structured, riskbased methodology that scales validation efforts appropriately to system
complexity and risk.
Software Categorization System
A critical component of GAMP 5 is software classification, which determines the
appropriate validation strategy:
- Category 3: Non-configured commercial off-the-shelf (COTS) products
- Category 4: Configured COTS products requiring functional testing
- Category 5: Custom applications demanding comprehensive validation
Understanding these categories enables validation teams to optimize resources
while maintaining regulatory compliance and system reliability.
Module 2: Data Integrity Fundamentals
Data integrity has emerged as a critical regulatory focus, with recent warning letters and enforcement actions highlighting its
importance. This dedicated module ensures participants understand both the principles and practical implementation of data integrity
controls.
ALCOA+ Principles
Attributable, Legible,
Contemporaneous, Original, Accurate
4plus Complete, Consistent, Enduring,
and Available. These nine principles
form the foundation of all data integrity
programs.
Audit Trail Management
Comprehensive coverage of audit trail
configuration, activation, review
procedures, and regulatory
expectations for computer-generated,
time-stamped records of all data
modifications.
Raw Data Protection
Best practices for defining, capturing,
storing, and protecting raw electronic
data from initial creation through longterm archival, ensuring data remains
trustworthy and retrievable.
Module 3: The Validation V-Model Lifecycle
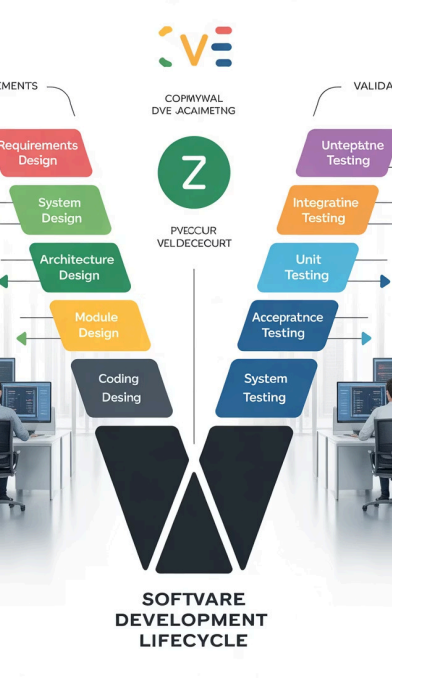
The V-Model represents the systematic, structured approach to validation
projects. This core practical module guides participants through each phase of
the validation lifecycle, from initial planning through final reporting.
1 Planning & Risk Assessment
Establish validation strategy, create Validation Plan (VP), and
conduct Functional Risk Assessment to identify critical system
functions.
2 Specification Phase
Develop User Requirements (URS), Functional Specifications (FS),
and Design Specifications (DS) defining system needs and
implementation.
3 Qualification Testing
Execute Installation (IQ), Operational (OQ), and Performance
Qualification (PQ) protocols to verify system compliance.
4 Documentation & Release
Complete Traceability Matrix and Validation Summary Report,
obtaining final approval for production use.
Specification and Qualification Phases
Left Side of V: Specification
The specification phase defines what the system must do and
how it will be built. Each specification document becomes
progressively more detailed:
- User Requirements Specification (URS): Captures business
needs and functional requirements from the end-user
perspective - Functional Specification (FS): Describes how the system will
meet user requirements at a functional level - Design Specification (DS): Provides technical details of
system architecture and configuration
These documents form the foundation for all subsequent testing
activities.
Right Side of V: Qualification
The qualification phase verifies that the system was built correctly
and operates as intended:
- Installation Qualification (IQ): Confirms proper installation,
configuration, and environmental conditions - Operational Qualification (OQ): Tests system functionality
and controls across their full operating range - Performance Qualification (PQ) / User Acceptance Testing
(UAT): Validates system performance under real-world
conditions
Each test protocol traces back to specific requirements, ensuring
complete coverage and regulatory compliance.
Module 4: Operation & Maintenance (System Assurance)
Achieving validation is only the beginning. Maintaining the validated state throughout the system’s operational life requires robust
procedures and ongoing vigilance. This module addresses the critical processes that ensure continued compliance.
Change Control
Formal processes to evaluate, approve, test, and document all
system modifications4including software updates, patches, and
configuration changes4preventing unintended loss of validated
status.
Configuration Management
Controlling and documenting the system’s defined state
throughout its operational lifecycle, ensuring consistency and
traceability of all system components.
Security & Access Control
Validation of user access management, authentication
mechanisms, password policies, and system security controls to
prevent unauthorized access or data manipulation.
Business Continuity
Disaster recovery planning, backup and restore validation, data
archival procedures, and periodic system reviews to ensure
ongoing compliance and data availability.
Emerging Approaches: Computer Software Assurance
A Paradigm Shift in Validation
Computer Software Assurance (CSA) represents the FDA’s evolving
approach to software validation, emphasizing critical thinking over
extensive documentation. This modern methodology acknowledges
that traditional validation approaches can be resource-intensive without
necessarily improving product quality or patient safety.
Core CSA Principles
- Risk-based testing focus: Concentrating efforts on critical
functionality rather than comprehensive documentation - Leveraging supplier documentation: Utilizing vendor testing and
quality systems for commercial software - Automated testing: Implementing continuous testing frameworks
that provide ongoing assurance - Reduced documentation burden: Streamlined records that focus on
critical decisions and test results
CSA represents the future of validation, balancing regulatory compliance
with modern software development practices and agile methodologies.
Building Your CSV Expertise
Core Curriculum Modules
Core Modules
Comprehensive curriculum covering
regulatory foundations through operational
maintenance
Compliance Focus
Aligned with FDA, EU, and international
GxP regulatory requirements
Qualification Phases
Systematic approach through IQ, OQ, and
PQ validation testing
Your Path Forward
This Computer System Validation training program provides the comprehensive knowledge and practical skills needed to excel in GxP
environments. From understanding regulatory requirements and data integrity principles to implementing the V-Model lifecycle and
maintaining validated systems, you’ll gain expertise across the full spectrum of CSV activities.
Whether you’re new to validation or seeking to update your knowledge with current best practices like Computer Software Assurance,
this curriculum equips you to ensure compliant, reliable computerized systems that protect product quality and patient safety. The riskbased, systematic approach you’ll master represents the industry standard for achieving and maintaining validation in today’s complex
regulatory landscape
